Thousands Linux and FreeBSD Servers Infected with Mumblehard Spamming Malware

The sophisticated Mumblehard spamming malware infects thousands of Linux and FreeBSD servers going under the radar for at least five years.
In the last seven months, several thousand Linux and FreeBSD machines have been infected with a sophisticated malware dubbed Mumblehard. The infected machines were part of a botnet used, in the last five years, to run spam campaign, a version of the Mumblehard malware was uploaded to the VirusTotal online malware checking service in 2009.
The researcher uncovered theMumblehard after being contacted by a system administrator who reported that its server was added to public security blacklists for sending spam.
The experts speculated that bad actors exploit vulnerabilities in Joomla and WordPress in order to compromise the server and install the Mumblehard malware.
Security experts at ESET have monitored the botnet during the last 7 months by sinkholing one of its C&C servers and observing 8,867 unique IP addresses connected to it, with 3,000 of them joining in the past three weeks.
“Mumblehard components are mainly Perl scripts encrypted and packed inside ELF binaries. In some cases, the Perl script contains another ELF executable with the same packer in the fashion of a Russian nesting doll.” states the report published by ESET. “Perl scripts were packed inside ELF binaries written in assembly language, showing a higher level of sophistication than average”
According to the ESET researchers, the Mumblehard malware was designed by a team of highly skilled programmers.
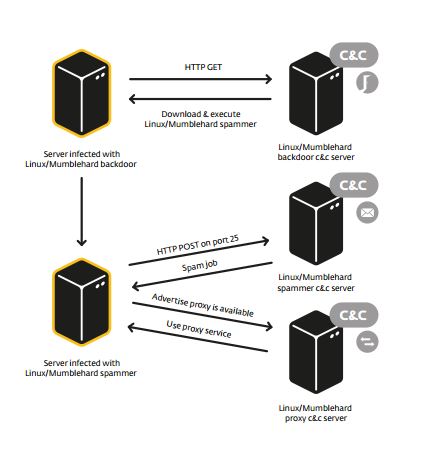
The experts analyzed two different strains of malware used by threat actors behind the malicious campaign, the first one is a generic backdoor that receives the list of commands from the C&C server by downloading and executing a file from a specific location. The second variant of malware is a spammer daemon.
The Mumblehard is malware is the demonstration of the increased level of sophistication for malware that target Linux ad BSD machines, despite the researchers consider the Windigo Operation discovered in 2014 much more complex.
Nonetheless, it is worrying that the Mumblehard operators have been active for many years without disruption.”
The experts discovered a link between the Mumblehard malware and the company Yellsoft, which sells DirecMailer, a Perl-based software for sending bulk e-mail. The researchers noticed that the IP addresses of C&C for the malware are the same assigned to the company.
The block of IP addresses for both Yellsoft and some of the Mumblehard C&C servers share the same range.
“The other is through the distribution of backdoored “pirated” copies of a Linux and BSD program known as DirectMailer, software that Yellsoft sells on their website for $240. The pirated copies actually install the Mumblehard backdoor (described later) that allows the operators to install additional malware. ” continues the report.
The block of IP addresses for both Yellsoft and some of the Mumblehard C&C servers share the same range.
“The other is through the distribution of backdoored “pirated” copies of a Linux and BSD program known as DirectMailer, software that Yellsoft sells on their website for $240. The pirated copies actually install the Mumblehard backdoor that allows the operators to install additional malware. “
Administrators can check the presence of the Mumblehard infection by looking for unexplained cronjobs that are added by the malware to contact the C&C servers 15 minutes. The backdoor is usually located in the /tmp or /var/tmp folders, to neutralize it is possible to mount the directories with the noexec option.
Comments are closed.