How to configure APACHE server with Self Signed Certificate on CentOS/ Red Hat Linux / Fedora
We need to follow below steps to configure APACHE with Self Signed certificate
[root@opensourceeducation ~]# yum install mod_ssl openssl
Loaded plugins: fastestmirror Loading mirror speeds from cached hostfile * base: mirror.atlanticmetro.net * epel: mirrors.mit.edu * extras: centos.mirror.nac.net * updates: mirror.ash.fastserv.com Setting up Install Process Package openssl-1.0.1e-16.el6_5.14.x86_64 already installed and latest version Resolving Dependencies --> Running transaction check ---> Package mod_ssl.x86_64 1:2.2.15-30.el6.centos will be installed --> Finished Dependency Resolution Dependencies Resolved ==============================================================================================================Package Arch Version Repository Size ============================================================================================================== Installing: mod_ssl x86_64 1:2.2.15-30.el6.centos updates 91 k
Transaction Summary ==============================================================================================================Install 1 Package(s)\ Total download size: 91 k Installed size: 183 k Is this ok [y/N]: y Downloading Packages: mod_ssl-2.2.15-30.el6.centos.x86_64.rpm | 91 kB 00:00 Running rpm_check_debug Running Transaction Test Transaction Test Succeeded Running Transaction Installing : 1:mod_ssl-2.2.15-30.el6.centos.x86_64 1/1 Verifying : 1:mod_ssl-2.2.15-30.el6.centos.x86_64 1/1 Installed: mod_ssl.x86_64 1:2.2.15-30.el6.centos Complete!
To Generate self certificates please follow below commands and add your information for your self singed certificate
[root@opensourceeducation ~]# openssl genrsa -out ca.key 2048 Generating RSA private key, 2048 bit long modulus ...................................+++ .........................................................................................+++ e is 65537 (0x10001) [root@opensourceeducation ~]# openssl req -new -key ca.key -out ca.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:PK State or Province Name (full name) []:ISB Locality Name (eg, city) [Default City]:ISB Organization Name (eg, company) [Default Company Ltd]:OSEN Organizational Unit Name (eg, section) []:IT Common Name (eg, your name or your server's hostname) []:OpenSourceEducation.net Email Address []:[email protected] Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []:pakistani An optional company name []: [root@opensourceeducation ~]# openssl x509 -req -days 365 -in ca.csr -signkey ca.key -out ca.crt Signature ok subject=/C=PK/ST=ISB/L=ISB/O=OSEN/OU=IT/CN=OpenSourceEducation.net/[email protected] Getting Private key
Now Copy all certificates and keys to /etc/pki/tls/ folders
[root@opensourceeducation ~]# cp ca.crt /etc/pki/tls/certs [root@opensourceeducation ~]# cp ca.key /etc/pki/tls/private/ca.key [root@opensourceeducation ~]# cp ca.csr /etc/pki/tls/private/ca.csr
Now Run below command to correct SELinux Contexts
[root@opensourceeducation ~]# restorecon -RvF /etc/pki
Now Open SSL.conf file to configure the APACHE SSL and replace the certificate / key paths
[root@opensourceeducation ~]# vi +/SSLCertificateFile /etc/httpd/conf.d/ssl.conf TransferLog logs/ssl_access_log LogLevel warn # SSL Engine Switch: # Enable/Disable SSL for this virtual host. SSLEngine on # SSL Protocol support: # List the enable protocol levels with which clients will be able to # connect. Disable SSLv2 access by default: SSLProtocol all -SSLv2 # SSL Cipher Suite: # List the ciphers that the client is permitted to negotiate. # See the mod_ssl documentation for a complete list. SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM:+LOW # Server Certificate: # Point SSLCertificateFile at a PEM encoded certificate. If # the certificate is encrypted, then you will be prompted for a # pass phrase. Note that a kill -HUP will prompt again. A new # certificate can be generated using the genkey(1) command. ###Please comment the below line and add the right path of the file below this line #SSLCertificateFile /etc/pki/tls/certs/localhost.crt SSLCertificateFile /etc/pki/tls/certs/ca.crt # Server Private Key: # If the key is not combined with the certificate, use this # directive to point at the key file. Keep in mind that if # you've both a RSA and a DSA private key you can configure # both in parallel (to also allow the use of DSA ciphers, etc.) ###Please comment the below line, add the right path of the files below this line and save the file using #SSLCertificateKeyFile /etc/pki/tls/private/localhost.key SSLCertificateKeyFile /etc/pki/tls/private/ca.key # Server Certificate Chain: # Point SSLCertificateChainFile at a file containing the # concatenation of PEM encoded CA certificates which form the # certificate chain for the server certificate. Alternatively # the referenced file can be the same as SSLCertificateFile # when the CA certificates are directly appended to the server # certificate for convinience. "/etc/httpd/conf.d/ssl.conf" 222L, 9568C written
Now Start or Restart the APACHE Server using below command
[root@opensourceeducation ~]# /etc/init.d/httpd restart Stopping httpd: [ OK ] Starting httpd: [ OK ] [root@opensourceeducation ~]#
After Apache configuration please add the 443 port into your IPtables firewall to accept incomming the connections
[root@opensourceeducation ~]# iptables -A INPUT -p tcp --dport 443 -j ACCEPT
[root@opensourceeducation ~]#service iptables save
Now please open your browser to check the web site is working
https://your-server-ip
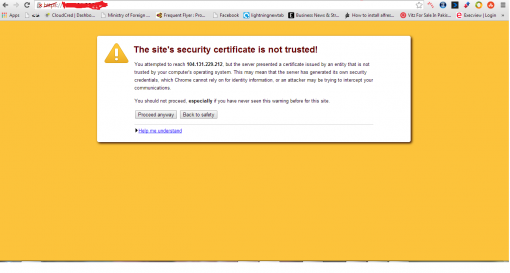
Now click on proceed anyway.
http://wiki.centos.org/HowTos/Https
Comments are closed.